How many times have you looked past the security signs that warn you that installing particular software could be dangerous for your computer? How many of us run untested programs with administrator privileges? In all likelihood, you would have done it countless times. In all honesty, we all have. Some users don’t even have an antivirus program installed or a firewall enabled. Now, a hacker group that goes by the name of Pegglecrew has shown us how this carelessness can cost us our important data.
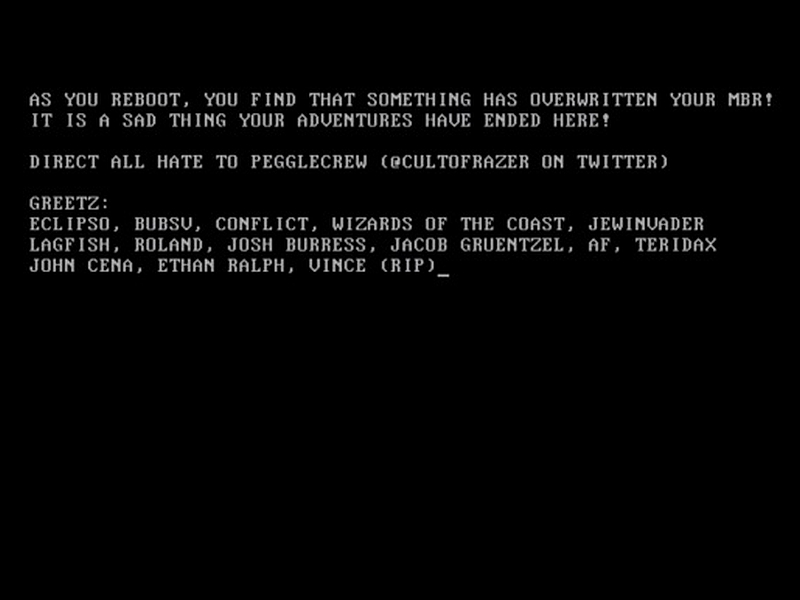
If you visited the website FossHub on Tuesday and downloaded either Classic Shell or audio editing software Audacity, you are at risk of having downloaded a Trojan that rewrites the user’s Master Boot Record (MBR) for Windows, and although nothing seems to happen at first, on rebooting the PC, you will find the following message:
As you reboot, you find that something has overwritten your MBR! It is a sad thing your adventures have ended here! Direct all hate to Pegglecrew (@cultofrazer on Twitter)
Notably, the @CultofRazer Twitter handle actually belongs to gaming firm Razer, and was hijacked for a while by the Pegglecrew team. The tweets posted detailing exploits have since been removed.
The entire thing seems harmless and childish as the infected code doesn’t do anything apart from rewriting the MBR, which contains information about the boot-up process of the computer. However, it should be pointed out that the hackers could have very easily stolen personal information from each of the infected computers. The hackers claimed to have attempted to install a rootkit, but gave up when they initially failed.
Explaining how the entire process panned out, a person who claims to be part of Pegglecrew said, “We were able to grab data from this network service to obtain source code and passwords that led us further into the infrastructure of FossHub and eventually gain control of their production machines, backup and mirror locations, and FTP credentials for the caching service they use, as well as the Google Apps-hosted email,” in an email to Softpedia.
Users seeing the message on startup will be unable to boot their computer unless they recover their MBR via the Windows recovery CD or other recovery options. You can can follow instructions posted by YouTuber ‘danooct1’ in his video here. Danooct1 also claims the infected binaries were not detected by file verification service Virus Total, and are largely identical in size to the originals.
Pegglecrew in one of its @CultofRazer tweets said it had managed compromise both Audacity and Fosshub servers, with the latter hack including the site admin’s email.
In a blog post by Audacity, it has acknowledged the incident, admitting one of its download servers had been compromised, and adding, “We have now replaced the 2.1.2 hacked windows installer and disabled that hacked account on FossHub.com – We are taking the incident very seriously indeed. We are working hard, in collaboration with FossHub.com, to do what we can to help prevent such an incident in future.”
FossHub has posted a separate apology on Reddit, where the company has explained how they had to shut down their primary server to prevent the spread of infected files and how its team members were not able to sleep for 30 hours.
Ironically, FossHub’s ‘About Us’ section on the website reads, “No adware, No spyware, No bundles, No malware, Fast downloads, Free services and a single ad. Most people like us.”
In a statement to Gizmodo, Pegglecrew detailed the reasons behind its hack, “We targeted Fosshub because we wanted inform people to keep better care of their security… all of the users actually clicked past a prompt telling them that it could be dangerous. That’s just one example of user carelessness and it barely amounts to the quantity of terrible passwords (also exploited in this attack) and other terrible practices.”
The entire incident goes to show how we all need to be more careful about the software that we install and depicts how disastrous the consequences can potentially be, if we are not. Audacity on its blog warns users should install antivirus programs and firewalls, and verify all files that they download before installing them by online file verification services like Virus Total. It also warns against deceptive advertising.
[“Source-Gadgets”]