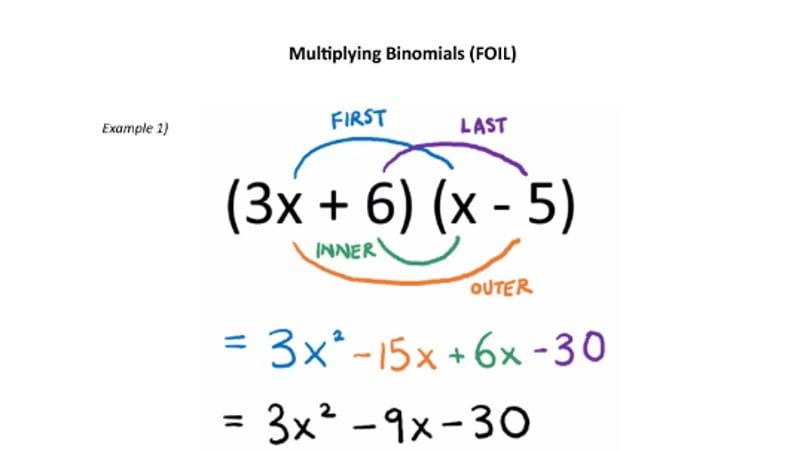
UK police on Tuesday arrested a 21-year-old man as part of their investigation into last month’s hack on VTech’s systems.
The man was arrested in Bracknell, 30 miles west of London, on suspicion of unauthorized access to a computer to facilitate the commission of an offense and suspicion of causing a computer to perform functions to secure or enable unauthorized access to a program or data, police said.
The South East Regional Organized Crime Unit, whose officers made the arrest, also seized a number of unspecified electronic items.
The Hack’s Targets
The breach affected more than 4.8 million parents’ accounts and nearly 6.4 million related child profiles, according to VTech.
About 1.2 million of the children had the Kid Connect app enabled. The app let them exchange voice and text messages, photos, and drawings between VTech tablets and smartphones.
The majority of the victims — about 2.2 million parents and 2.9 million kids — were in the United States.
VTech suspended Learning Lodge, the Kid Connect network and several websites to allow Mandiant, a subsidiary of security firm FireEye, to conduct a security assessment and help beef up security.
The Threat to Kids
Parent data taken includes names; email, mailing and IP addresses; secret question and answer for password retrieval; the password itself; and download history.
Kids’ profiles on VTech listed only their names, genders and birthdates, VTech said, but someone claiming to be the hacker told Motherboard he obtained the kids’ head shots and chat logs.
“Even the name, gender or birthday of children in the wrong hands is a concern,” pointed out Brian Laing, VP at Lastline.
Such information can allow a predator to establish familiarity with a potential victim, he told the E-Commerce Times.
The Impact of the Arrest
The arrest “will have the same impact on cybercrime as a high-profile drug bust has on international drug trafficking: none,” said Jeff Hill, channel marketing manager at Stealthbits.
“The potential financial rewards so far outweigh the risk of being caught that resource-constrained international law enforcement currently serves as a nonexistent deterrent, and that’s likely to be the case for the foreseeable future,” he told the E-Commerce Times.
An Angel in Disguise?
The hacker who breached VTech’s systems did so to call attention to the company’s poor cybersecurity practices, he told Motherboard. He reportedly feared the company would ignore him if he approached it directly.
There was evidence indicating others previously might have accessed the data, the hacker said, and he claimed he didn’t want to publish the data or profit from it.
“Society’s perception of a criminal’s motives is irrelevant,” Hill pointed out. “An unarmed man who jumps the White House fence and enters the front door to highlight security vulnerabilities is a criminal, irrespective of his arguably virtuous intent.”
Assuming best case or best intentions “is a mistake,” Lastline’s Laing contended. The stolen data could be used to access an online VTech account and hack into a toy that allows voice collection to let the hacker gather information on a family.
Hackers potentially could push out dangerous messages to toys that could speak once they’d broken into a consumer’s online account, he suggested.
“How would your child respond if their toy suddenly said, ‘Mommy needs you to open the front door right now’?” Laing asked.
Beefing Up Security in Connected Toys
Companies making connected toys or other Internet of Things appliances “need to really think seriously about security” and perhaps hire security companies specializing in application testing, Laing said.
However, security in connected toys likely will come about because of “a general reluctance of customers to embrace toys and applications that require the submission of personal information to operate,” Stealthbits’ Hill suggested, as well as manufacturers acceding to that trend.
[“source-technewsworld”]